




As modern software development evolves, integrating application security (AppSec) into every phase of the SDLC is critical. Developers, QA engineers, DevOps professionals, and IT leaders must build foundational skills in secure coding, threat modeling, and automated security testing. Certifications like OSCP and CSSLP and platforms like Hack The Box and Secure Code Warrior, offer practical training to close the AppSec skills gap. Embracing AppSec helps reduce vulnerabilities, enhance compliance, and future-proof your software delivery pipelines, making it a strategic advantage for both individuals and organizations navigating today’s cloud-native, fast-paced tech landscape.
We live in a time when software eats the world, and application security (AppSec) is becoming a must-have competency, not just for cybersecurity specialists but also for developers, DevOps engineers, testers, and IT leaders. Security can no longer be a reactive process addressed in the final stages of development. The shift toward DevSecOps means that every stakeholder in the software development lifecycle (SDLC) shares responsibility for securing applications from the ground up.
Modern development demands faster releases, distributed teams, and cloud-native architectures, all of which introduce new vulnerabilities and attack surfaces. Traditional perimeter-based security models aren’t enough when microservices, APIs, and containers are in play.
Some key stats driving this urgency:
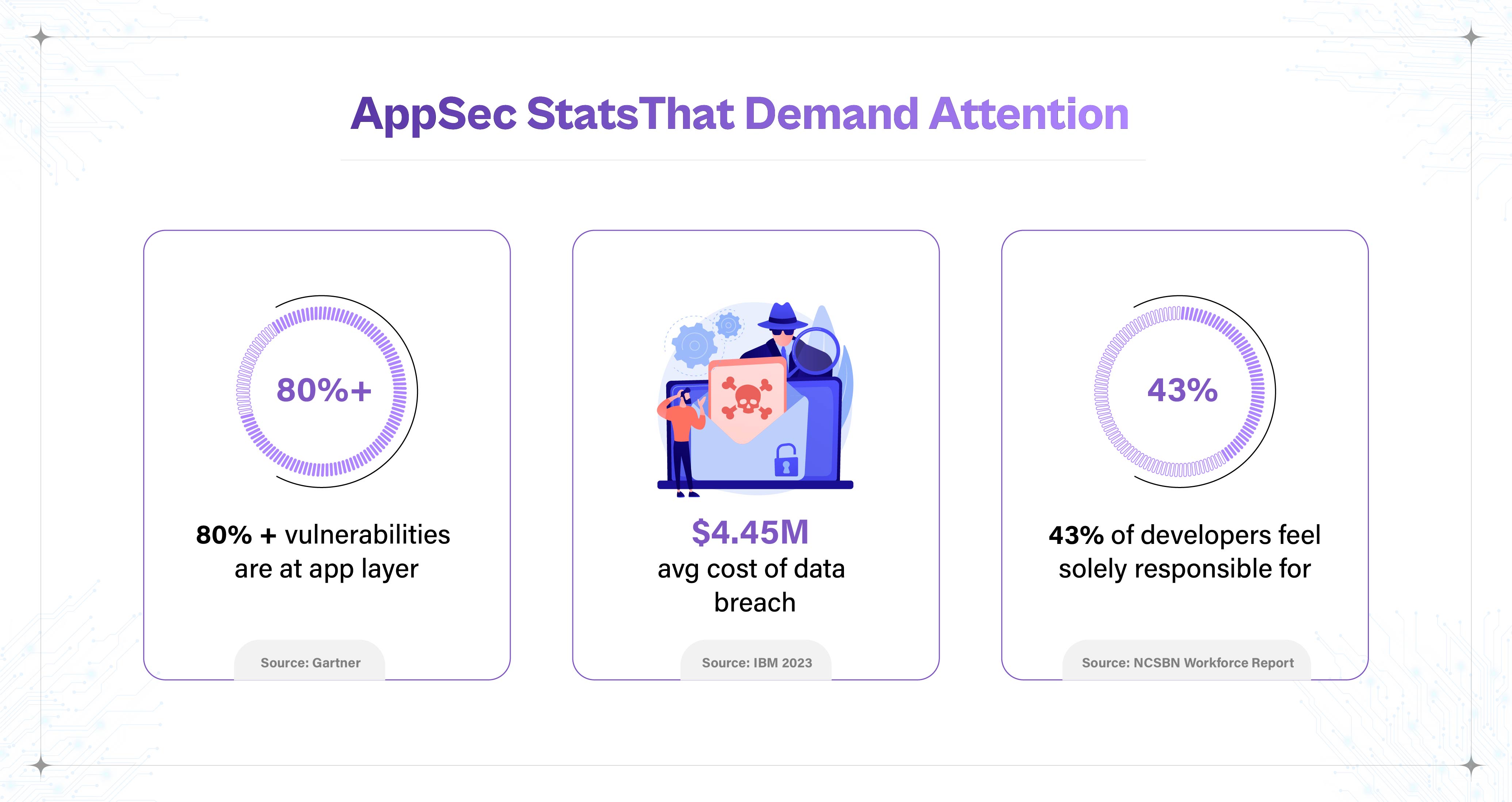
In this landscape, upskilling in AppSec isn’t just a career booster; it’s a strategic imperative. Whether you're a developer aiming to write more secure code or a team lead building secure pipelines, understanding security fundamentals and tools is crucial.
Today’s developers are expected to be more than just feature builders. They must also think like attackers to prevent them. Secure coding practices, like input validation, proper authentication, and safe error handling, are no longer niche concerns; they’re table stakes.
Upskilling in AppSec enables developers to:
From a management perspective, investing in AppSec training leads to:
Furthermore, AppSec training fosters a culture of ownership and awareness. Developers become more security-conscious, QA teams align test cases with security requirements, and DevOps teams embed security into infrastructure as code.
Below we highlight ten of the most respected and effective AppSec courses and certifications, including OSCP, CSSLP, and top offerings from SANS and Security Compass, to help you build resilient, secure applications and advance your career.
Ideal For: Software developers, security architects, and engineers involved in the software development lifecycle (SDLC)
Key Features:
Benefits:
Ideal For: Penetration testers, red teamers, ethical hackers, and security analysts
Key Features:
Benefits:
Ideal For: Security professionals, penetration testers, and ethical hackers
Key Features:
Benefits:
Ideal For: Developers, security architects, and application security professionals
Key Features:
Benefits:
Ideal For: Cloud security engineers, DevOps professionals, and application developers
Key Features:
Benefits:
Ideal For: Developers, DevOps teams, and security professionals
Key Features:
Benefits:
Ideal For: Web developers, QA engineers, and security testers
Key Features:
Benefits:
Ideal For: Software developers and engineers
Key Features:
Benefits:
Ideal For: Architects, DevSecOps, and security analysts
Key Features:
Benefits:
Ideal For: All technical roles
Key Features:
Benefits:
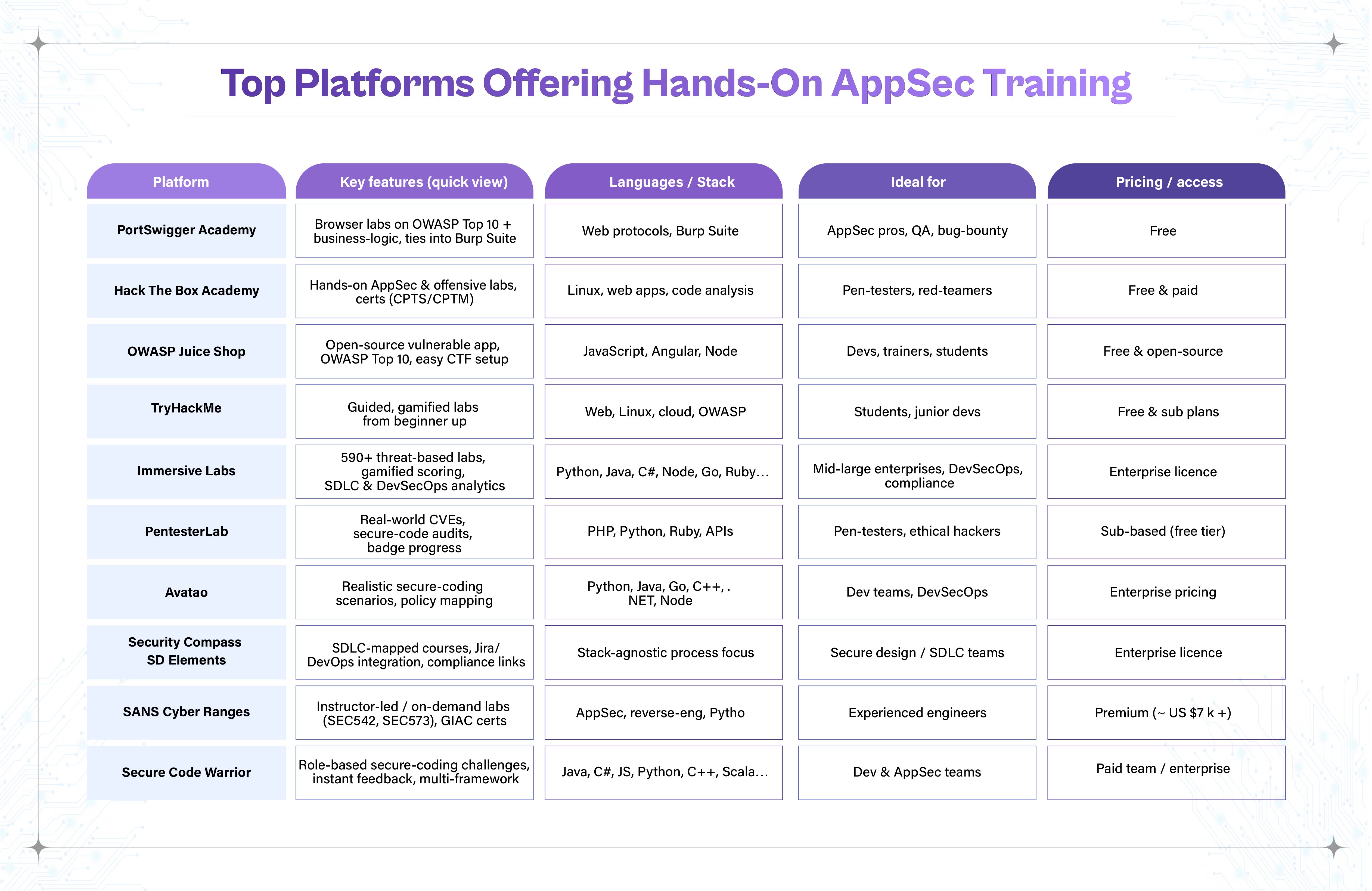
Along with certifications and training, here’s a curated list of the top platforms offering hands-on lab training for Application Security (AppSec). These platforms are known for immersive, real-world environments that help developers, security professionals, and DevSecOps teams build and test secure coding skills.
Application Security (AppSec) is no longer the exclusive domain of traditional security professionals. As security becomes integrated into every phase of the SDLC (Software Development Lifecycle), professionals from development, QA, IT operations, and DevOps backgrounds are increasingly finding natural transitions into AppSec roles.
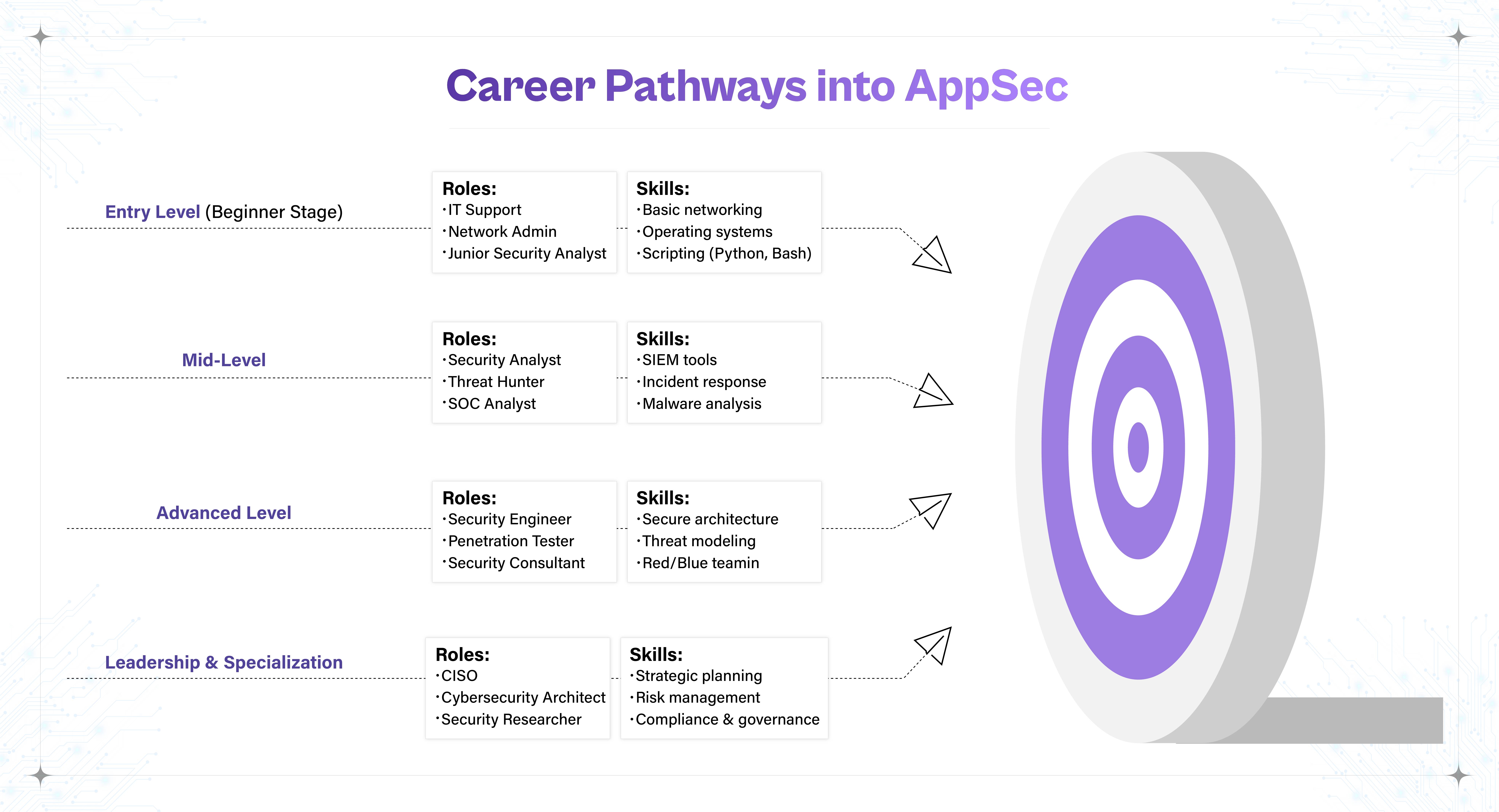
Here's how each pathway typically unfolds:
Developers already understand how applications are built and deployed, which gives them a significant head start in identifying and fixing security flaws. The transition often begins with:
Many developers start by becoming the "security champion" in their team, someone who bridges the gap between security and engineering, before moving into dedicated AppSec or Secure DevOps roles.
QA professionals already have a firm grasp of testing methodologies, workflows, and edge-case thinking skills essential to finding application vulnerabilities. Their transition path typically includes:
QA engineers often become security-focused testers, and in some cases, move further into vulnerability management or penetration testing roles.
Operations and support professionals familiar with networks, systems, or incident response can pivot to AppSec by focusing on:
This route often feeds into cloud security engineering or DevSecOps roles where both infrastructure and application security overlap.
Regardless of your background, a few enablers accelerate AppSec transitions:
In the modern SDLC, software engineers are expected to build secure-by-design applications.Here are the key skills future-focused developers should cultivate:
By embedding security into the coding mindset, software engineers become critical players in preventing vulnerabilities early in the pipeline.
Security champions are developers or QA engineers embedded within teams who promote secure practices. They act as the first line of defense and liaison between the security team and development squads.
Key responsibilities include:
Organizations like Microsoft and Adobe have formal security champion programs. Studies have shown that teams with embedded security champions reduce mean time to vulnerability remediation (MTTR) by up to 30%.
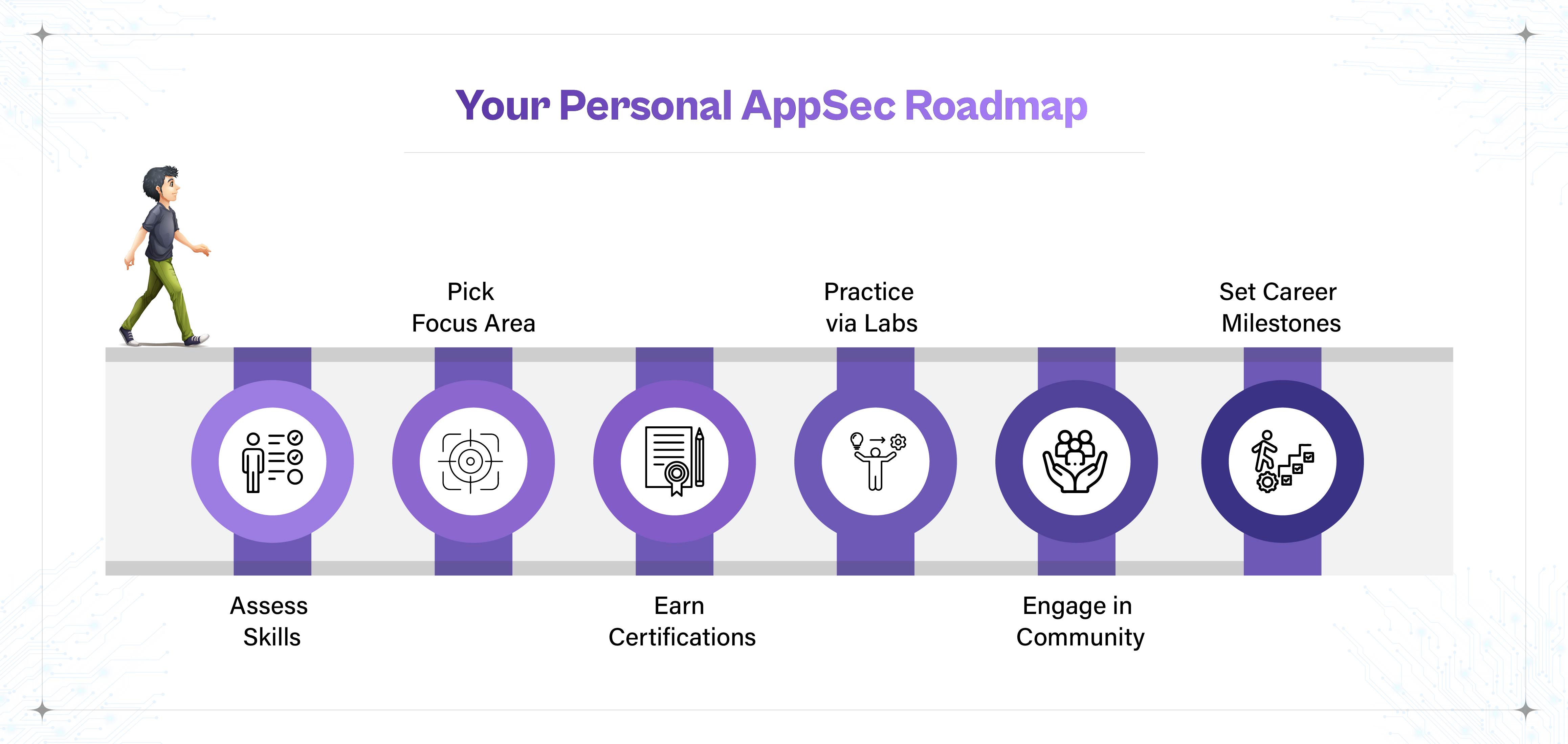
Upskilling in AppSec isn't a one-size-fits-all journey. Developers, testers, and IT professionals can create a personal roadmap aligned with their roles and interests. Key steps include:
A structured plan improves focus and shows measurable progress, especially useful for developers planning to transition roles or justify upskilling to their managers.
The AppSec field is growing fast, and organizations actively seek professionals with cross-functional experience in security. With the right training and guidance, transitioning into AppSec is feasible and highly rewarding.
Application security has become a critical skill set for today’s software professionals. As development cycles accelerate and systems become more complex, the responsibility for securing applications can no longer rest solely with dedicated security teams. Developers, testers, and IT professionals alike are expected to integrate security thinking into their everyday work.
Upskilling in AppSec is not just a smart career move it’s a strategic one. It empowers teams to identify risks early, reduce costly vulnerabilities, and build software that stands up to real-world threats. Whether you’re aiming to write more secure code, strengthen your CI/CD pipeline, or transition into a specialized security role, the right knowledge and tools make all the difference.
The journey doesn’t have to be overwhelming. With the growing availability of hands-on labs, certifications, and structured learning paths, building AppSec capabilities is more accessible than ever. Investing in these skills today means contributing to more resilient applications and shaping a more secure future for everyone who depends on them.
Whether you're enhancing your current role or planning a career transition, the right training can make all the difference. Contact us today and begin your AppSec learning journey now!
The rich text element allows you to create and format headings, paragraphs, blockquotes, images, and video all in one place instead of having to add and format them individually. Just double-click and easily create content.
A rich text element can be used with static or dynamic content. For static content, just drop it into any page and begin editing. For dynamic content, add a rich text field to any collection and then connect a rich text element to that field in the settings panel. Voila!
Headings, paragraphs, blockquotes, figures, images, and figure captions can all be styled after a class is added to the rich text element using the "When inside of" nested selector system.
Ever wondered how computer programming works, but haven't done anything more complicated on the web than upload a photo to Facebook?
Then you're in the right place.
To someone who's never coded before, the concept of creating a website from scratch -- layout, design, and all -- can seem really intimidating. You might be picturing Harvard students from the movie, The Social Network, sitting at their computers with gigantic headphones on and hammering out code, and think to yourself, 'I could never do that.
'Actually, you can. ad phones on and hammering out code, and think to yourself, 'I could never do that.'
